Thursday, January 01, 2004
It's the end of the world as we know it …
And I feel fine.
Resolutions for this year?
- Do not make resolutions I cannot keep.
- … um …
So. There you go.
Friday, January 02, 2004
It was a dark and stormy night …
I say, bleah. Brevity is the soul of wit, and this goes on and on and on and then it goes on and on and on some more and then it goes on for a bit after that. Long, long, long. Much funnier, sez I, is the likes of this:
Jennifer stood there, quietly ovulating.
The Bulwer-Lytton Fiction Contest requires one to write the most horrible opening sentance to a novel; the Lyttle Lytton Contest is the same, only you are restricted to 25 words or less, which makes for funnier openings, such as:
Monica had exploded, and I had a mystery, and pieces of her pancreas, on my hands.
B. Otter
or
For centuries, man had watched the clouds; now, they were watching him.
S. Sachs
Great stuff here. Now I just need to come up with a horrible opening line to a novel.
Yet another blogging award type thang
And speaking of contests, there is also BlogMadness 2003, where participants enter what they consider to be their best entry of 2003. Sounds interesting, so I combed through the entries for 2003.
It's sobering that I didn't really find that many entries I liked. It was quickly narrowed down to two entries, a three line entry (six lines if you include the title) and the Fourth of July entry, with pictures.
As much as I liked the three line entry, it was this picture that won out, so that was the entry I entered. I can only hope I at least I get some technical award or something.
Sunday, January 04, 2004
Referrer spam
It appears, b!X pointed out, that “Joe Lieberman is advertising his website by hitting unrelated websites to which it does not link, passing along false referer information that points people to the joe2004.com website.”
I've checked my own referer logs for this month (January) and I haven't seen the Joe Leiberman referer spam, although I did see Wesley Clark referer spam (I guess if it's good for one, it's good for the other) and plenty of sites hawking the Paris Hilton (although why the Paris Hilton needs such advertisements is beyond me—are they going bankrupt there or something?). And in an incredible display of tackiness or cluelessness (or both!), I got referer spam from StarProse Corporation which has an article about how bad referer spam is.
And Andrew Jackson is still the most popular thing being linked to here.
Why I did what I did during a DDoS attack
While looking for referer spam I found that my entry about fending off a DDoS attack has been quite popular, but upon rereading I found it rather terse. So I figure I might as well clear up some details of what exactly I did.
netstat -an to check the state of all network connections,
and given that there were an enormous number of connections in the
SYN_RECV state is an indication that a SYN flood
(where hundreds of connections are initiated but not completed, thus
flooding out legitimate traffic) is underway.
Normal TCP/IP networking is open to an attack known as “
SYNflooding”. This denial-of-service attack prevents legitimate remote users from being able to connect to your computer during an ongoing attack and requires very little work from the attacker, who can operate from anywhere on the Internet.
SYNcookies provide protection against this type of attack. If you sayYhere, the TCP/IP stack will use a cryptographic challenge protocol known as “SYNcookies” to enable legitimate users to continue to connect, even when your machine is under attack. There is no need for the legitimate users to change their TCP/IP software;SYNcookies work transparently to them. For technical information aboutSYNcookies, check out <http://cr.yp.to/syncookies.html>.If you are
SYNflooded, the source address reported by the kernel is likely to have been forged by the attacker; it is only reported as an aid in tracing the packets to their actual source and should not be taken as absolute truth.Help from the Linux Kernel 2.4 Configuration screen
sysctl -w net.ipv4.tcp_syncookies=1 is the command used to
enable SYN cookies in the Linux kernel. This helps some with
the type of attack we were experiencing.
sysctl -w net.ipv4.tcp_max_syn_backlog=2048 increases the
number of incomming connections the kernel can keep track of. Increasing
this value is a bit of a double edged sword in such an attack—on the one
hand, we allow more connections, thus hopefully allowing legitimate
connections through, but on the other hand, we allow more connections, thus
allowing more machines to SYN flood the machine. Given some of
the other steps I took, this was probably a good idea overall.
sysctl -w net.ipv4.tcp_syn_retries=2 (which I forgot to
mention in the original entry) decreases the amount of time the kernel
spends trying to establish a TCP/IP connection (from a default
value of 5 attempts to two) which helps to flush the bad connections from
the system quicker.
route add -host <ip-addr> reject which causes the
kernel to ignore packets from the given IP address, and also flushes current connections from
said IP addresses from the
system. This was the thing I was doing that kept the system up and
running during the attack. I ended up writing a script to continuously
check the connections, then once a certain threshhold of bad connections was
exceeded, ban all the addresses.
The site was eventually taken down dispite all the attempt I made to keep it up since the network traffic to the site in question was swamping the rest of the network the machine was on (it was the colocation facility that said enough is enough and shut the site down). Other than that, I was fairly successful in keeping the website accessible.
Some notes on being a writer
… how do you become an author?
I always give the same answer: it's easy to be an author, whether of fiction or nonfiction, and it's a pleasant profession. Fiction authors go about making speeches and signing books. Computer authors go to computer shows and then come home to open boxes of new equipment and software, and play with the new stuff until they tire of it. It's nice work if you can get it.
The problem is that no one pays you to be an author.
To be an author, you must first be a writer …
The secret of becoming a writer is that you have to write. You have to write a lot.…
I am sure it has been done with less, but you should be prepared to write and throw away a million words of finished material. By finished, I mean completed, done, ready to submit, and written as well as you know how at the time you wrote it. You may be ashamed of it later, but that's another story. [emphasis added]
Jerry Pournelle: How to get my job
I would think that after four years of doing this I would have a million words done by now, but nooooo. I only have about 340,000 words of material here.
Heh. Only.
Only 660,000 bad words left to write.
By contrast, I suspect that Atlas Shrugged (by Ayn Rand) has about half a million words (only it feels twice as long). And Jerry Pournelle's The Mote in God's Eye (okay, him and Larry Niven) has about 224,000 words in it.
Can you tell I'm trying to pad my count with worthless entries?
Finally I get to see it
I finally got to see Return of the King today, and I found it well worth the price of admission and not at all did it feel like a three and a half hour film.
However, the Coke and popcorn was not worth the $9 I paid. Ouch.
Monday, January 05, 2004
More stuff
I came downstairs to find the Computer Room had exploded and a distraught Spring trying to piece it together again.
Okay, it didn't literally explode—just that the stuff in there finally got to Spring so she started tossing items out of the Computer Room. In this case, pretty literally tossing items out of the Computer Room (I'm still finding bits and pieces of a former mouse that didn't survive—not that it deserved to live anyway).
To calm her down, I gave her the task of sorting through a box of papers, tossing out the garbage, keeping the important stuff. She didn't quite understand why I had her do that when the rest of the room (and the front entry hall way) was still in a state of mess, but there was method to my madness; basically, get her out of the room and concentrating on something else while I finished cleaning up the area around the Computer Room.
Once she was done with the sorting, I had her file everything in the box. She still wasn't clear why I was having her do such seemingly inconsequential tasks, but such inconsequential tasks (which weren't all that inconsequential) were calming her down.
In the mean time, I had pretty much finished with cleaning up the Computer Room and front entry hall and the mountain of stuff seemed more managable. And it's certainly more roomy in the Computer Room now.
The rest of Dillinger's desk is not far behind
The VKB attaches to handhelds and projects the image of a full-size keyboard onto the surface of the desk where the handheld is placed, allowing the user to input text without a physical keyboard.
Via Vidicon, First Virtual Laser Keyboard Coming in a Few Months
Not quite in the same league as Dillinger's desk in Tron, this is still quite cool (and amazingly enough, there doesn't seem to be a picture of Dillinger's desk on the Internet—wierd because it's such a cool desk).
There are all kinds
It's 2004, and we aim to make it the YEAR OF HEADPHET! We're really starting to see more and more images appearing in popular culture featuring our favourite subject—sexy ladies in headphones, headsets, ear defenders and all the rest of that good stuff. Of course, the only way this can continue is for each and every one of you to do your part to ensure this site—and its sister sites—grows during this year.
Via Michael Duff, Headph0ne Phet1sh
While I find this surprising, at the same time, I don't find it surprising at all.
Tuesday, January 06, 2004
He failed to fail.
On 2003 April 5th, a Saturday, at the age of 33, I threw away my dignity, mocked my Ivy League education, disgraced my Master's degree, and proved, in just over three hours, that humans can do things “The System” didn't anticipate. Things didn't turn out exactly as planned, but it was a crazy experience!
Via Kisrael, Scholastic Aptitude Test: Answering All Questions Incorrectly
A most amusing tale of a man who set out to fail, and failed!
Well, he didn't exactly achieve his goal of getting the absolutely lowest score on the SAT but you'll have to read it to find out where he failed to fail.
Wednesday, January 07, 2004
Tell me again how easy Windows is to keep running …
My goal was to see how much time I waste in a typical month on computer problems/maintenance. Prior to this experiment, I had a vague notion that I was spending a fair amount of time on this kind of stuff. This experiment has brought the actual amount of time into sharp focus.
Having done the experiment, it is amazing to me how many problems a tiny home network can create. Over the course of one month, I logged 21 different errors/problems/activities that wasted time.
Via The Gus, Marshall Brain's Blog: Amazing Amount of Time Wasted Repairing Computers in December
I've been using the same computer now for … um … six years or so and I haven't had nearly the amount of problems that Marshall had in one month. Then again, I'm running Linux (RedHat 5.2 in case you were wondering, and probably weren't) and except for the times I masochistically torture myself, I haven't had any problems with Linux (or Unix for that matter).
To be fair, I haven't had as many problems with Windows as Marshall, but when I do, they tend to be rather spectacular and no amount of swearing, blasphomy or sacraficing small furry animals will fix the problem (even reinstalling Windows would fail—I don't mean fail to fix the problem, I mean the installation itself would fail). That's why I pretty much stick with what I have.
Saturday, January 10, 2004
How AOL handles their email
A discussion Mark and I were having turned towards email—specifically, sending email to AOL. He's communicating with some people who use AOL and is concerned about his email getting through. He heard that AOL had proposed some new DNS record and was curious if I heard anything about it. I had not, but I started doing a Google search.
Going through the results, I came across a link to the AOL Postmaster Info page, a document that describes how AOL handles email and the criteria they use to accept or reject email. There is some very good information here (for all the ribbing AOL gets from the rest of the Internet, their infrastructure and networking architecture is incredible and they certainly know what they're doing technically, if only to handle the millions of subscribers).
Monday, January 12, 2004
A huge ever growing pulsating bee that rules from the center of the bedroom
[This is mostly true. Mostly.] The alarm clock went off as usual, and as usual, I rolled out of bed, crossed the gulf of the room where the clock was and slapped the snooze button, rolled back into bed. It's a ritual I've been doing for the past decade or so. I purposely put the clock out of arms reach from the bed in the hopes that the physical act of climbing out of bed would help wake me. It doesn't work; I can not only navigate the treacherous waters of the bedroom floor with my eyes closed, but with my mind closed as well. I've also learned to sleep through other noises that would wake most people, including the dead. Yet there is one sound that can penetrate the deep fog of sleep—that of an insect flying.
Odd how the sound of a leaf blower won't disturb me even if it's inside the same room, yet the soft buzzing of a mosquito drives me insane. Yet the buzzing I heard this morning after the first hitting of the snooze button didn't sound like a mosquito.
My initial thought was those XXXX kids, what are they up to now? but for some reason I rejected that answer. I then thought that perhaps this was some far off lawn mower or leaf blower but the pitch didn't seem quite right.
Nine minutes of pondering later, I do the roll-snooze-roll routine.
More buzzing. More pondering. Perhaps one of the neighborhood kids on one of those motorized scooters, I thought. Or if it is one of The Kids, they're going to get it! Yet more buzzing. It sounds too much like an insect thought. Like a bee or something. I could delude myself into thinking it was something else, but the buzzing …
Not even nine minutes have passed and I'm out of bed, turning off the alarm clock and slowly tracking the buzzing noise. Sounds like its coming from behind the blinds. Definitely coming from behind the blinds. Carefully I reach towards the chain to rotate the blinds and right there—
BEE!
staring at me, my visage repeated thousands of times across the facets of its compound eyes as it cooly reguarded me staring at complete horror at this … this … invader of my sanctuary. It fluttered its wings, as if to confirm that yes, I am the one responsible for this buzzing sound, mind if I sting you to death now? I quickly closed the blinds and fled the room, screaming like a little girl.
Quick digression: I should mention that I do not know if I am allergic to bee stings or not—I've never been stung or bitten (except by the occasional mosquito) and at this late stage of the game, I'm not too keen about finding out the hard way. Okay, back to the story.
“Um … Spring,” I said.
“Yes?” said Spring.
“Could you do me a huge favor?”
“What is it?”
“There's this huge ever growing pulsating bee that rules from the center of the bedroom,” I said. “Could you take care of it?”
Spring gave me this rather odd look. “A huge ever growing … ?”
“Bee.”
“Bee.”
“That rules from the center of the bedroom,” I said.
“A bee?”
“Yes.”
“I see. And you want me to take care of this huge ever growing pulsating bee that rules from the center of the bedroom?”
“Please?” I said. Bambi eyes.
A giggle from Spring as she got up from the couch. “Yes, I can take care of it,” she said.
“You're not allergic, right?”
“To bees, no. Wasps, yes,” she said. We headed up the stairs. Spring carefully cracked the door to the bedroom open and slipped in. “Where did you last see it?”
“Behind the blinds.”
“You might want to close the door,” she said. “We don't want it to get loose in the house.”
“Good idea,” I said. I still don't fully understand how I ended up on the other side of the door, outside the bedroom. But the door was closed—the bedroom sealed off, along with Spring. Mano a aguijón. May the best combatant win. I stood there, just outside the door, anxiously awaiting; listening to the muffled sounds of the epic struggle filtered through the door, refusing to imagine what must be going on inside the bedroom.
Minutes pass. More muffled sounds of an epic struggle.
The door suddenly opens, Spring springs out, door shut. Took longer to read that than it took for the action to actually happen. Spring looks concerned. “There are now two huge ever growing pulsating bees that rule from the center of the bedroom,” she said. “And I don't think they're bees. I think they're—
WASPS!
It doesn't look good,” she said. I went to The Kids' bedroom and looked out. To my horror I saw a swarm of huge ever growing pulsating wasps engulfing the Facility in the Middle of Nowhere, blanketing the place; the din of buzzing rising in my ears as my mind tried to retreat into its Happy Place. “We're going to have to call The Office,” she said. “Maybe they can do something.”
Nuke the site from orbit. A stray thought fired in my mind. It's the only way to make sure, was the other stray thought. Guess I won't be grocery shopping, a third thought that crashed into the other two. But then we're out of food! forced its way throught the other three struggling thoughts and I knew we were in trouble.
A few minutes later and it's worse than it appears. “Tomorrow?” asked Spring. She was on the phone to The Office, informing them of the huge ever growing pulsating swarm of killer wasps that rules from outside Facility in the Middle of Nowhere. “The exterminators can't come until tomorrow? I see. Thank you.”
I leave these notes so that future generations may know the horror that was unleased here at the beginning of the 21st century.
Breaking the law! Breaking the law!
Ah … wierdness in law. It seems that Adobe® added code to Adobe® Photoshop® to prevent images of currency to be manipulated using said program. In the discussion on Slashdot, USC Title 18 Part I Chapter 25 §504 came up. Relevent bits:
(i) all illustrations shall be in black and white, except that illustrations of postage stamps issued by the United States or by any foreign government and stamps issued under the Migratory Bird Hunting Stamp Act of 1934 may be in color;
(ii) all illustrations (including illustrations of uncanceled postage stamps in color and illustrations of stamps issued under the Migratory Bird Hunting Stamp Act of 1934 in color) shall be of a size less than three-fourths or more than one and one-half, in linear dimension, of each part of any matter so illustrated which is covered by subparagraph (A), (B), (C), or (D) of this paragraph, except that black and white illustrations of postage and revenue stamps issued by the United States or by any foreign government and colored illustrations of canceled postage stamps issued by the United States may be in the exact linear dimension in which the stamps were issued; and
(iii) the negatives and plates used in making the illustrations shall be destroyed after their final use in accordance with this section. The Secretary of the Treasury shall prescribe regulations to permit color illustrations of such currency of the United States as the Secretary determines may be appropriate for such purposes.
USC Title 18, Part I, Chapter 25, §504
I may be breaking the law.
According to (i) above, all illustrations have to be in black and white, except for certains stamps that fall under the Migratory Bird Hunting Stamp Act of 1934 (code). But (ii) above states that all illustrations have to be larger or smaller than actual size, unless they are in black and white! at which case, they can be actual size.
Blink. Blink.
(iii) is pretty explicit, although I'm now concerned I may have to destroy my scanner.
You see, it all comes down to the most linked image on my site—that of Jeff
Conaway Andrew Jackson. I
scanned the image off the new US $20 bill
(well, not so new now) and while I don't have the full US $20 bill being displayed, I do have the portrait that is
fairly close to actual size (at least on my monitor) and it's in color (okay,
black and green). So, I'm either violating provision (i) above (by having it
in color) or (ii) above (by having it near actual size) and (iii) by virtue
of not having destroyed the image or scanner, although technically speaking,
the scanner does not have plates, and the concept of a “negative” is
pretty tenuous, so I may not have to destroy my scanner.
But the size issue does concern me. I could check against a real US $20,
but my wallet is currently in the bedroom, and there's this huge ever growing pulsating bee wasp that
rules from the center of the bedroom so the actual check will have to
wait.
But if the check does prove that the image of Andrew Jackson is smaller or larger than actual size (“Really officer! Check out the image here on my 72″ monitor—see! That doesn't match the actual size at all!”) I'm still probably violating provision (i) above by having it in color. I suppose I could just delete the image entirely and solve this and other problems but that still doesn't actually answer the question of “Am I breaking (or have I broken) the law?”
And it sucks that it would cost me $400 to have a lawyer go “Don't know, but delete it anyway just to make sure, unless you really want to test this in a court of law in which case hand over your bank account.”
Update
According to Adobe®, I need to include trademark information whenever I mention Adobe® or any Adobe® products, like Adobe® Photoshop®. Thanks to Kisrael for the heads up.
Adobe and Photoshop are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries.
Tuesday, January 13, 2004
I, for one, welcome our new Vespoidea masters
“Those aren't wasps,” said the exterminator. “They're yellow jackets!”
Idiot, thought Spring. Yellow jackets are wasps. “Can you do anything about them?”
“Let me suit up,” he said. He walked out to his truck. A few minutes later he comes back. “Sorry, we don't do yellow jackets.”
“Excuse me?”
“We don't do yellow jackets. We need to refer you to another company.”
“Another company? You don't do wasps?”
“Yellow jackets.”
“Wasps, yellow jackets, who cares? You don't exterminate them?”
“Nope. Those things are dangerous!”
So we are stuck with our Vespoidea friends until Thursday!
Thursday!
Lovely.
This was the news I got upon waking (the bit above is a reconstruction of events that happened earlier in the day). Spring had also bought some wasp spray, one can with a range of 15′ and one with a reach of 22′, just in case. She also checked out our bedroom, which yesturday was being lordered over by a pair of Paravespula vulgaris. Several minutes pass as I wait outside the closed door.
“They don't appear to there anymore,” said Spring.
“Did you check by the closet?” Outside the building, they're swarming around the portion of the Facility in the Middle of Nowhere that corresponds to our closet.
“No, let me check.” Spring went back into the bedroom for several minutes, then came out. “I was afraid to mess too much with the right side of the closet. I could hear them.”
“That's not good,” I said.
“Buzzing around, and what sounds like some scratching from inside the wall,” she said.
“Inside the wall?”
“Yes,” she said. “It didn't sound like wasps; more like a scratching noice, like mice or something.”
“In the deaththrows of being stung to death, I don't doubt.” Great! They may be inside a section of wall!
But they don't appear to be inside the room, and Spring did spray around the areas most likely for them to crawl through. So the room should be safe.
Should.
And they don't appear to bother anyone coming or going in or out of the Facility in the Middle of Nowhere so several much needed trips to the grocery store ensued.
Thursday.
Inside the wall.
Can I scream now?
On the plus side, The Office is paying for this. Not us.
Update on Wednesday, January 14th, 2004
Spring presents her side of the yellow jacket story.
In my defense, I have such a horrible memory for dialog (so of course I became a Drama Geek in high school), unlike some friends of mine, like Gregory, who can recite whole swaths of diaglog verbatim from a film he's only seen once while for the life of me I can't remember what was said to me mere moments before.
Thus, the embellishments.
But then again, all you need do is read The Demonic Creature that Invaded Bill's Room to see just how wild my embellishments can get.
The Johnson Automatic Perspective Machine
Mark hired me to do some HTML work for his company. Basically, jazz up some pages for a demo of his product, Seminole. So I figured some graphic images, a logo-type deal, would be nice for the hypothetical, Internet enabled toaster we're doing for a demonstration (later on, we might add a consumer grade router type device, but I'm still getting used to his templating system and working with what he's done so far). I'm not that graphically savvy to create logos and whatnot so I decided to check the net to see if there were public domain clip art that could be appropriated.
 There does exist a nice body of public domain clip art,
but not much that is accessible by website. Sure, there are websites that
will sell you CDs and books of public domain clip art (such as Dover
Publications), but they don't make it directly available via their
sites.
There does exist a nice body of public domain clip art,
but not much that is accessible by website. Sure, there are websites that
will sell you CDs and books of public domain clip art (such as Dover
Publications), but they don't make it directly available via their
sites.
But I did find two sites that had some Victorian/Edwardian era clip art.
I have a thing for late 1800/early 1900 line art.
 During the 80s, Wendy's design motif was
turn-of-the-century and all the counter and table tops where decorated in
old advertising. I used to love reading the various advertisements
and gaze at wonder at the line art. The intricate detail. The cross
hatching. The various line weights. Beautiful stuff.
During the 80s, Wendy's design motif was
turn-of-the-century and all the counter and table tops where decorated in
old advertising. I used to love reading the various advertisements
and gaze at wonder at the line art. The intricate detail. The cross
hatching. The various line weights. Beautiful stuff.
And now I'm drooling over Heck's Pictorial Archive of Nature and Science (which inspired many of the O'Reilly book covers), Heck's Pictorial Archive of Military Science, Geography and History and Heck's Pictorial Archive of Art and Architecture.
Drool. Drool. Drool.
 But guess what Ftrain should showcase
(besides the Johnson Automatic Perspective Machine, write for particulars to
Shaw & Johnson, Tampa, Fla) but hundreds of magazines from the late 1800s to early 1900s, with tons
and tons of public domain Victorian/Edwardian clip art. All online.
But guess what Ftrain should showcase
(besides the Johnson Automatic Perspective Machine, write for particulars to
Shaw & Johnson, Tampa, Fla) but hundreds of magazines from the late 1800s to early 1900s, with tons
and tons of public domain Victorian/Edwardian clip art. All online.
Drool.
Wednesday, January 14, 2004
“There is a multilegged creature crawling on your shoulder … ”
It's dark outside. The temperature is falling (64°F currently, expected low of 51°F) so the threat of our Vespoidea masters should be less. Or so I thought. The Kids were outside tearing apart an old scooter they found and asked for some help in removing some bolts.
I'm kneeling on the ground, hunched over, holding a wrench steady on one bolt while The Younger attempts to remove another one lower down on the bolt when The Older one said “Sean?”
“Yes?” I notice he has this crazed look in his eye.
“There's a wasp,” he said.
I felt a slight tickling on my back. “It's on my back, isn't it?” The Older, not blinking, staring in horror as Paravespula vulgaris crawls around my back. The Older starts to get up. “For the love of God and all that is Holy don't do anything!” I calmly said.
The Kids were frozen in their tracks, staring at my back as Death Incarnate crawled around on my shirt. I for one stopped breathing, least I invoke an attack of aggression.
Time stood still.
The seconds stretched into eons.
Eventually, I heard the buzzing of a wasp flying away.
“Is it gone?” I asked.
“Yes—”
I was already inside, door shut tight.
“Hey! What about us?”
Oops.
Thursday, January 15, 2004
We leave them alone, they leave us alone
It seems I was a mistaken the other day about how long our Vespoidea master will be around. The original exterminator said he'd be back on Thursday but then backed out, claiming another company will handle our little friends. So there's no telling when this other company will actually get around to kicking some Paravespula vulgaris butt. We'll have to remember to call The Office to get updates.
It's not too bad—the wasps are no longer getting inside our bedroom, and the other good thing about this is that The Kids are no longer climbing on top of the storage area, that being right below Vespoidea central.
Hide the Remote
One of the little games The Kids play is “Hide the TV Remote.” One of the little games I play is “Find the XXXX Remote That The Kids Have XXXXXXX Hid Yet Again!” The Kids assure me that their hiding of the TV remote is a purely unconscience act on their part. They just … loose it from time to time.
So far, I've found the remote under the chair, under either of the two couches we have, under the cusions of the chair or the couches, underneath pillows, behind the TV, behind the sterio, on the dining room table, under the dining room table, on the kitchen counter, in the freezer and their closet, which is upstairs.
They just … loose it.
This came up yet again, tonight, because I wanted to watch Real Genius (which a friend of Spring gave to us). Twenty minutes of “Find the XXXX Remote That The Kids Have XXXXXXX Hid Yet Again!” and I've had enough.
“I believe it's time to forbid The Kids from using the TV remote,” I said to Spring.
“Why not hide it on them?” she asked.
“Good question,” I said. “Why not?”
So I did.
Muahahahahahahaha!
Friday, January 16, 2004
“That's the fifth dragon I killed in one shot! What are the chances of that happening?”
For several months now, Bob has been attempting to run his weekly D&D game partially online—that is, former members who now live in other states are now “attending” the weekly gaming session online. To help facility this, Bob bought enough licences so we all can use kLoOge.Werks, a program that allows a DM to run his campaing online. And being written in Java, it does indeed run on multiple platforms (which is why I can run the thing under Linux; everybody else in the game uses Windows).
It's not perfect, but since the introduction of kLoOge.Werks (for several months we were trying other technologies) the gaming sessions have gotten a bit smoother and aren't quite as annoying as when Bob first started this little experiment. But the one thing I really dislike about this online gaming thang is the dice rolling.
You see, you use the kLoOge.Werks program to do your dice rolling.
As a programmer, I know that computerized dice rolling is anything but random. Pseudorandom, yes. But as random as real dice? Not by a long shot. It's actually difficult to get decent random numbers out of a computer; Knuth spent about 300 pages of rigorous material covering the generation of random numbers in his Art of Computer Programming. And I've told Bob as much.
But he is insistent on using kLoOge.Werks.
Durring a protracted combat session where the fighters are slugging it
out, “rolling” the dice, I decided to poke around the kLoOge.Werks
program. The Knoppix
live-CD I'm using on my laptop not
only has Java, but quite a few Java development tools, including a Java
disassembler. So I start poking around the .class files that
comprise kLoOge.Werks, telling Bob that it wouldn't be that much effort to
replace a few of the classes dealing with dice rolling with a special
version where I can “roll” what I want, including the DM-eyes-only
rolls.
Muhahahahahahahaha.
Which brings up another point about running a game online—trust. Forget the random number generators for a second, how can the master program (which the DM runs) trust that the “dice rolls” of the players are legit? Now you are getting into cryptography, digital signatures and verification, which aren't easy to do right and all too easy to get wrong. Bruce Schneier took over 700 pages to cover computerized cryptographic systems and even then, it's just an overview.
In the end though, I think this actually comes down to trust—that Bob will hae to trust his players not to muck around with kLoOge.Werks, and be suspicious if we all start rolling critical hits each time we attack.
Saturday, January 17, 2004
Porn porn porn porn
A week or so ago, Mark, JeffK and I ended up talking about “porn.” Not necessarily the topic of pornography, but the term “porn” itself. I had mentioned that CNN was “news porn.” Mark and JeffK had never heard of porn in that context, and I had to explain that in the context of “porn” is an excessive repetative content on a single topic. Hence, CNN is news porn, FoodTV is food porn, Cartoon Network is 'toon porn.
I first encounted that usage of “porn” in Synners, by Pat Cardigan (way back in the early 90s) and I found the concept both intriguing and quite on target. And while such usage of “porn” is still somewhat rare, it's not uncommon:
1990s moviegoers who have sat clutching their heads in both awe and disappointment at movies like “Twister” and “Volcano” and “The Lost World” can thank James Cameron's “Terminator 2: Judgment Day” for inaugurating what's become this decade's special new genre of big-budget film: Special Effects Porn. “Porn” because, if you substitute F/X for intercourse, the parallels between the two genres become so obvious they're eerie. Just like hard-core cheapies, movies like “Terminator 2” and “Jurassic Park” aren't really “movies” in the standard sense at all. What they really are is half a dozen or so isolated, spectacular scenes—scenes comprising maybe twenty or thirty minutes of riveting, sensuous payoff—strung together via another sixty to ninety minutes of flat, dead, and often hilariously insipid narrative.
Via kisrael.com, F/X Porn
Which makes a good a generic definition of “porn” as anything. And puts CNN into a whole new light …
Monday, January 19, 2004
“Your poutfoo is no match for me!”
It seems that The Kids found out where I hid the remote. The Younger strode into the Computer Room and headed straight for it. “No,” I said. “You are not to get the remote.”
“But why not?” said the Younger. “I need it!” He gave me his angry pouting stare, and sat down on the other chair in the room. Well, it's not actually sitting per se, more of a squirming ever moving sitting.
“Do you know why I'm hiding it?”
“Yea,” he said. “Mom told us earlier.”
“So you realize it's because I hate playing ‘Find the Remote’ every single night. So no more remote for you.”
The Younger then switched to his pouty-angry stare, sat there whining and squirming for another few seconds, then ran off. Two minutes later he completely forgot about the remote and was yelling at his brother to switch the channel.
And to think I was worried that The Kids just didn't care about the remote and my actions would have no effect.
Muahahahahahahaha.
Tuesday, January 20, 2004
The next wave in web advertising, only it doesn't seem to work
Unicast is extremely proud to introduce the long-awaited Video Commercial—the new online ad format that delivers full screen, television-quality video for advertisers.
The 2 MB, 30-second spots exhibit broadcast—not broadband—quality video larger than any other format and allows advertisers to build interactivity into their sophicsticated offline assets.
Delivered via our patented, fully pre-cached method, the Video Commercial is the only formst that plays perfectly for every consumer, every time up to 8 times faster than broadband video.
If there are typos in the above quote, it's my fault, since the text is being rendered by Flash, which of course means you can't cut-n-paste.
Okay, who let the marketers out? And why does anyone listen to them? Every consumer? Every time?
Now I'm curious. I read further into the site:
30-seconds of pure video and expanded interactivity shown perfectly to every consumer every time.
Use full-screen, broadcast quality video to bring your advertising messages online. The [2 MB] Video Commercial plays without any ‘freezing’ or ‘buffering’ and up to 8 times faster than most broadband video units to ensure your campaigns play as well on the Internet as they do on Television.
Somebody better call John Ashcroft—these people are obviously smoking something illegal. Eight times faster than broadband, and at broadcast quality? Okay, this I have to see. I selected the “View Examples” link:
Warning
Your browser does not accept cookies. You must enable cookies to continue with this demo.
Okay, so there goes their claim of “every consumer, every time.” Didn't work for me. So it's not “every time.” And I could have sworn I had cookies enabled. Yup. I do. Okay, I enabled cookies based upon privacy settings of “medium,” so I crank the setting down to the lowest setting possible and reload the page.
Warning
Your browser does not accept cookies. You must enable cookies to continue with this demo.
Okay … damn the security, full cookies ahead!
Warning
Your browser does not accept cookies. You must enable cookies to continue with this demo.
Well heck!
If they can't get this to work under Windows XP and Mozilla, then there is no way they can claim “every consumer, every time.” No XXXXXXX way. I tried all the formats, all the demos, and not one worked for me. Not one!
I hope no one paid these jokers any money.
Then again, I'm not using IE …
Like I said, who let the marketers out? And who's responsible for listening to them?
Can you verb a noun? Or even a website?
Spring setup the account. Surprising, to say the least.
Actually, I had given it some thought to mirror my entries here in my own LiveJournal account (which I use to leave comments, and my friends page is a handy way to keep up with a dozen or two friends who also have LiveJournals) but really, I like the idea that I only post to my LiveJournal once a year.
The only problem I see is that now it's all too easy to see when I actually write these entries (I tend to predate entries quite often).
Wednesday, January 21, 2004
How to measure 5/6 cup of oil and other math follies
I'm not quite sure how to approach this subject. Spring is home schooling The Kids and has spent quite a bit of money on school books (captive audience, much like college textbooks). But on the other hand, The Kids would have these textbooks if they were going to regular school, so I figure it would be fair (if expensive) game to write about the quality. It's not like there are other text books out there Spring could get.
Like I said, captive audience.
[Evaluating schoolbooks] was a pretty big job, and I worked all the time at it down in the basement. My wife says that during this period it was like living over a volcano. It would be quiet for a while, but then all of a sudden, “BLLLLLOOOOOOWWWWW!!!!”—there would be a big explosion from the “volcano” below.
The reason was that the books were so lousy. They were false. They were hurried. They would try to be rigorous, but they would use examples (like automobiles in the street for “sets”) which were almost OK, but in which there were always some subtleties. The definitions weren't accurate. Everything was a little bit ambiguous—they weren't smart enough to understand what was meant by “rigor.” They were faking it. They were teaching something they didn't understand, and which was, in fact, useless, at that time, for the child.
Finally, I come to a book that says, “Mathematics is used in science in many ways. We will give you an example from astronomy, which is the science of stars.” I turn the page, and it says, “Red stars have a temperature of four thousand degrees, yellow stars have a temperature of five thousand degrees …”—so far, so good. I continues: “Green stars have a temperature of seven thousand degrees, blue stars have a temperature of of ten thousand degrees, and violet stars have a temperature of … (some big number).” There are no green or violet stars, but the figures for the others are roughly correct. It's vaguely right—but already, trouble! That's the way everything was: Everything was written by somebody who didn't know what the hell he was talking about, so it was a little bit wrong, always! And how we are going to teach well by using books written by people who don't quite understand what they're talking about, I cannot understand. I don't know why, but the books are lousy; UNIVERSITY LOUSY!
Anyways, I'm happy with this book, because it's the first example of applying arithmetic to science. I'm a bit unhappy when I read about the stars' temperatures, but I'm not very unhappy because it's more or less right—it's just an example of error. Then comes the list of problems. It says, “John and his father go out to look at the stars. John sees two blue stars and a red star. His father sees a green star, a violet star, and two yellow stars. What is the total temperature of the stars seen by John and his father?”—and I would explode in horror.
“Judging Books by Their Covers,” “Surely You're Joking, Mr. Feynman!” by Richard Feynman.
So I see one of The Kid's math book on the desk and I remember Richard Feynman's rant on text books from the 60s. Universally bad then, are they still just as bad now?
Gazpacho
From a math text book no less!
Ingredients:
- 6 green onions
- 6 ripe tomatoes
- 1 clove of garlic
- 1 green pepper
- 1 slice of bread
- 2 tbsp olive oil
- 2 tbsp lemon juice
- pinch of salt
- ½c cold water
That's it! That's all the recipe they give!
Sigh.
It's certainly more colorful than math books I had in school (although to tell the truth, I don't really remember any prior to sixth or seventh grade—this might be a fifth grade book, which marks it as The Older's book) and it's very Politically Correct with kids of all nationalities and ethnicities present. Scanning through the Table of Contents, I see that Chapter 10 (“Working With Fractions”) has a “food” theme. Fractions, food. Yea, I can kind of see that … maybe. I flip to Chapter 10 and start paging through it.
I get to the section about dressing the salad, which is about adding fractions with different (“unlike”) denominators:
Paul likes to mix his own salad dressing. He adds 5/6 cup of olive oil and ¼ cup of vinegar to the contents of a packet of seasoning to complete the mixture. How much liquid does Paul add?
 My first thought was, I usually mix equal parts oil and vinegar.
Interesting to see what the actual recipe is. Then, as I looked at the
picture, my next thought was, Five sixths? How the hell did Paul measure
out five sixths? Okay, slight digression. 2/6 is 1/3, and 1/3 cup
measures I have. So 2/3 brings us almost there, but the final 1/6? I had
to pour through several cookbooks to find five tablespoons and one teaspoon
is equivalent to 1/3 cup, so to halve that you need … 2½
tablespoons and ½ teaspoon. I have ½ teaspoon measures,
multiple in fact, but a ½ tablespoon? I have a single 1½
tablespoon measure. So Paul here uses a 1/3 cup measure (or 2/3 cup measure
if he has one) a tablespoon measure, a 1½ tablespoon measure (if he
has one) and a ½ teaspoon measure to get 5/6 cup of oil. And Paul,
who is anal enough to dirty four measuring devices in order to get
exactly 5/6 a cup of oil, resorts to using prepackaged
seasonings? Some chief!
My first thought was, I usually mix equal parts oil and vinegar.
Interesting to see what the actual recipe is. Then, as I looked at the
picture, my next thought was, Five sixths? How the hell did Paul measure
out five sixths? Okay, slight digression. 2/6 is 1/3, and 1/3 cup
measures I have. So 2/3 brings us almost there, but the final 1/6? I had
to pour through several cookbooks to find five tablespoons and one teaspoon
is equivalent to 1/3 cup, so to halve that you need … 2½
tablespoons and ½ teaspoon. I have ½ teaspoon measures,
multiple in fact, but a ½ tablespoon? I have a single 1½
tablespoon measure. So Paul here uses a 1/3 cup measure (or 2/3 cup measure
if he has one) a tablespoon measure, a 1½ tablespoon measure (if he
has one) and a ½ teaspoon measure to get 5/6 cup of oil. And Paul,
who is anal enough to dirty four measuring devices in order to get
exactly 5/6 a cup of oil, resorts to using prepackaged
seasonings? Some chief!
Or rather, out of sixteen authors, not one can cook! Or even cares enough to use realistic measurements if they're going to bother to use cooking as a theme!
Lourdes wants to learn to cook Portuguese soup. Her grandmother said that the chorizos—spicy Spanish sausages—are the secret to making this soup. Chorizos can be bought at markets that have Spanish or Latin American foods.
About how many cups of beans are needed for Portuguese soup?
Portuguese Soup
Ingredients
- 3 lb beef roast
- 2 tbsp oil
- 3 onions
- 6 c water
- 1 1/8 c dried kidney beans
- 1 7/8 c dried pea beans
- 3 or 4 chorizo sausages
- 4 c cabbage
- 3 or 4 c broccoli florets
- 1 lb spinach
What? You expect cooking directions from a math book?
We never hear about chorizos again, so why put it in? Remember, this is a math book, not a cook book, so that first paragraph appears to be a non-sequitur.
Anyway … getting back to about how many cups of beans are in Portuguese Soup. Notice in the recipe how you have to have 1 1/8 c dried kidney beans, but oh … 3 or 4 sausages. Not 3 1/3 sausages. 3 or 4. But never five. And not two. Unless you then proceed to three, or four, your choice. But remember to measure out an additional 1/8 cup of dried kidney beans (hint: two tablespoons).
Now, the point of this section is to teach rounding of fractions. And yes, while I can immediately see that 1 1/8 + 1 7/8 is about 3 (for exact values of 3) but a fifth grader might not see that, so I can see the value in learning estimation. But a soup recipe is already a bunch of estimates! I bet the original recipe called for a cup of kidney beans and two cups pea beans and one of the sixteen authors fudged the numbers a bit to make this example, obviously oblivious to the fact that 1/8 cup measures don't exist and even if they did, the margin of error in measure beans exceeds the exactness of the very measure!
I can begin to see where Feynman was going. At first thought, using cooking to teach fractions does seem like a good idea, so I'm happy there. But I'm a bit unhappy that the authors pick unrealistic measures for some of the ingredients, and I'm very unhappy that if they are going to waste space listing ingredients at least finish up the recipe so that if a student is intrigued enough to try the food, they can (and learn just how unrealistic this math book—which on second thought, is probably why they didn't include the rest of the recipes!).
Also, if I were writing the text, I'd ask how much cabbage is needed; it's a trick question since broccoli is a type of cabbage (muahahahahahaha—methinks I've been watching too much Real Genius lately).
- Suppose you need to make 6 pounds of fruit salad.
- You already have 2¼ pounds of strawberries, melon, and grapes. How much more fruit do you need?
- You decide to buy blueberries, kiwi, and raspberries. You buy 1½ pounds of blueberries and 3/4 pounds of kiwi. How many pounds of raspberries do you need to buy?
- You want to double the recipe. How much will you have of each kind of fruit?

- Okay …
- Trick question—you already have too much, you need to remove fruit.
- Is this instead of the existing fruit? In addition? You still have either way too much, or you really like raspberries.
- Let's see … you have equal parts strawberries, melon and grapes, but we haven't fully established if we are adding blueberries, kiwi and raspberries or not, so it's hard to establish rations of these additions; who the hell wrote this question anyway?
What finally clinched it, and made me ultimately resign, was that the following year we were going to discuss science books. I thought maybe the science books would be different, so I looked at a few of them.
The same thing happened: something would look good at first and then turn out to be horrifying. For example, there was a book that started out with four pictures: first there was a wind-up toy; then there was an automobile; then there was a boy riding a bicycle; then there was something else. And underneath each picture is said, “What makes it go?”
I thought, “I know what it is: They're going to talk about mechanics, how the springs work inside the toy; about chemistry, how the engines of the automobile works; and biology, about how the muscles work.”
I turned the page. The answer was, for the wind-up toy, “Energy makes it go.” And for the boy on the bicycle, “Energy makes it go.” For everything, “Energy makes it go.”
Now that doesn't mean anything. Suppose it's “Wakalixes.” That's the general principle: “Wakalixies make it go.” There's no knowledge coming in. The child doesn't learn anything; it's just a word!
“Judging Books by Their Covers,” “Surely You're Joking, Mr. Feynman!” by Richard Feynman.
Update on Thursday, January 22nd, 2004
“Sean,” said Spring, “what did you mean by there being too much fruit?” She obviously just finished reading this entry.
“There were 2¼ pounds each of strawberries, melon and grapes,” I said.
“I think they meant 2¼ pounds total of strawberries, melon and grapes,” she said. “Other than that, you were spot on.”
“Oh,” I said. “I guess I need to work on my reading comprehension skills.”
“And your spelling. There were quite a few mistakes.”
“Well, I didn't take them to task for spelling; it was a math book after all.”
So the question about the fruit salad does make some sense now, but still, the third part is quite involved—there is no indication of how much each of strawberries, melon and grapes you have, so you have to assume an equal portion of each, and is a fifth grader smart enough to divide 2¼ by 3 and get 3/4?
Update on Wednesday, February 20th, 2019
D.J. wrote in with a simpler way to measure ⅚ cups. It's better than what I have above.
Update on Saturday, May 11th, 2024
Somebody used this entry to help measure out ⅚ cups. Yeah, I couldn't believe it either, but there it is. I have also found much better way to measure out ⅚ cups if you ever need to.
Update on Thursday, August 22nd, 2024
And yet, there's an even simpler method!
Friday, January 23, 2004
For all your computing commuting needs …
Very cool! A mobile computing lab is up for auction at eBay (link received via a mailing list I'm on). And since I expect that the page won't last very long, I snagged some pictures for future prosperity.
And there are some pretty cool features:
- Lighting, heating, air conditioning & ventilator powered by separate Onan 7.5 kilowatt diesel generator with a remote start switch inside vehicle
- 21 occupant maximum seating capacity
- 4 duplex electrical outlets for on board 110 volt service
- 1 retractable projection screen
- emergency lighting in case of power failure
- 2 NEW roof top Air Conditioner units
And if that weren't enough, someone else sent in a link to the Steelwheels Project, the ultimate in offroad winnebago living. The electrical system alone is impressive:
- 8 killowatt diesel skid mounted 120 volt dual leg auto start/stop generator, water cooled
- 3000 watt inverter with power share and 130 amp charger
- Engine room main 30 amp breaker with 8 circuit panel
- 12 volt alternator 310 amp internal regulator
- 120 volt Heavy Duty rooftop air conditioner with armour cover
Oh, and the communication system:
- roof mounted broad band sattelite system with laptop computer modem control
- sattelite radio
- moving map GPS with voice prompting
- CB radio
The bus is a bit less expensive ($15,000 starting) than the Steelwheels Project ($549,000.00, delivery in Canada or Continental United States included) but it looks so sweet …
Saturday, January 24, 2004
A twisty passage of Windows, all fragile
The
HLTinstruction tells the CPU to shut itself down until the next hardware interrupt. This is a big win on laptops since it reduces power consumption and thereby saves your lap from third-degree burns.We (well, specifically, Jeff) had this implemented and working in Windows 95 but discovered to our dismay that there were many laptops (some from a major manufacturer) which would lock up unrecoverably if you issued a
HLTinstruction.So we had to back it out.
Then the aftermarket
HLTprograms came out and people wrote, “Stupid Microsoft. Why did they leave this feature out of Windows.” I had to sit quietly while people accused Microsoft of being stupid and/or lazy and/or selfish.
Hardw are Backwards compatibility
From Mark come a pointer to Raymond Chen's weblog, a developer from Microsoft. An amazing insight into Microsoft development, covering why they did what they did, and >why they do what they do.
Even if you aren't a developer for Microsoft Windows, it's still facinating reading, such as this little bit:
CreateMenu creates a horizontal menu bar, suitable for attaching to a top-level window. This is the sort of menu that says “File, Edit”, and so on.
CreatePopupMenu creates a vertical popup menu, suitable for use as a submenu of another menu (either a horizontal menu bar or another popup menu) or as the root of a context menu.
If you get the two confused, you can get strange menu behavior. Windows on rare occasions detects that you confused the two converts as appropriate, but I wouldn't count on Windows successfully reading your mind.
What' s the difference between CreateMenu and CreatePopupMenu?
From reading Raymond's blog, it seems that Microsoft goes to great lengths to protect mediocre programmers and keep their programs running; their backwards compatibility legacy is quite impressive (I can still run an editor written in 1982 under MS-DOS 1.0 on Windows XP, some twenty-two years later). With so much legacy code (MS-DOS versions 1.0 (1981) through 7.x (1995) and Windows 1.0 (1985) through Windows XP) it's no wonder Windows is such a mess, much less that it still runs.
Monday, January 26, 2004
Technobabble technobabble technobabble
It took awhile, but I finally finished revamping my homepage. Perhaps the major reason it took so long was my enthusiam for dealing with XSLT waxed and waned over the past year. I got most of the way there by January of last year, but the resulting XML files of my site were not that well organized, and the XSLT file was a huge mess I could barely understand a few hours after writing it; it doesn't help that XSLT is quite verbose.
Just how verbose?
Before I can get there, I have to be a bit verbose myself and explain that the XML format I created looks a bit like:
<site directory="/">
<section directory="writings/">
<subsection directory="murphy/"> … </subsection>
<subsection directory="hypertext/"> … </subsection>
…
</section>
<section directory="photos/">
<subsection directory="top10/"> … </subsection>
…
</section>
…
</site>
The “site” (which is considered a “node”) is composed of several “sections” (again a “node”), each of which is composed of “subsections” (yet another type of “node”). Each node has a “directory” attribute, where the resulting HTML files will reside. There's a bit more (like individual pages) but that's enough to hopefully explain this wonderful bit of XSLT verbosity:
<li> <a href="../{preceding-sibling::subsection[@listindex != 'no'][position()=1]/attribute::directory}" title="{preceding-sibling::subsection[@listindex != 'no'][postition()=1]/child::title}"> Previous </a> </li>
That's one line of XSLT code there (broken up over several so you won't have to scroll all the way to the right). The nasty bit:
{preceding-sibling::subsection[@listindex != 'no'][position()=1]/attribute::directory}
comes into play when we're processing a template for a
<subsection>, and in English (as best as I can translate
it is):
Of the list of subsections that come prior to you in the current section, select those that do not have an attribute of listindex equal to “no” then select the first one in that list, then retrieve the value of the directory attribute.
Because if you don't specify the position(), you get the
last one (which in this case would be the first subsection in the section
that does not have the listindex attribute set to “no”) not the first node
(even though technically it's the last node in the list of preceding nodes,
and following-sibling works as expected—which makes a perverse type of
sense in a Zen like way). Got it? Good. Because I barely grok it
myself.
What it generates is something like:
<li> <a href="‥/murphy/" title="Murphy's Law"> Previous </a> </li>
Which is a link (within an HTML list) to the previous subsection.
That line comes in the middle of a section of XSLT code that, loosely translated into pseudocode, reads:
when in a subsection
choose
when listing nodes in order
if there exists a following node that is not hidden
print "... Next ... "
end-if
if there exists a preceding node that is not hidden
print "... Previous ... "
end-if
end-when
...
end-choose
end-when
Only not as succinctly (I'm viewing the code in a window 144 characters wide, and each line still wraps around). COBOL is terse compared to XSLT. And imaging writing about a thousand lines like that.
I did give serious consideration to using something else other than
XSLT to convert my site from XML to HTML, but the alternatives
weren't much better; I could have used Perl and XML::Parser,
but then I would have to explicitely crawl the resulting tree for
appropriate nodes (the addressing methods in XSLT, while verbose and
sometimes inexplicably odd, do make it easy to grab nodes) and the logic for
generating the pages, but code to dump out nodes verbatim. For instance, I
have sections like:
<body> ... HTML formatted as XML ... </body>
and to avoid having to write endless templates for things like
<P> and <BLOCKQUOTE>, in XSLT, I
just dump such sections out like:
<xsl:copy-of select="./node()"/>
Which does a literal copy of all the children nodes of the current node. If I were to use Perl, I would have to code this myself (the same consideration for using any other programming language with an XML parser really). Kind of six of one, half-dozen the other.
And seeing how I already had written a few thousand lines of XSLT (previous versions, revisions, etc., etc.) I decided to stick with what I started and see it through.
But now that I have this massive XSLT file, I don't really have to mess with it anymore. I can now just add content to the XML file that represents my site (I was able to add a photo gallery in about fifteen minutes of work, mostly spent typing the descriptions, without having to worry about adding navigation and images), then regenerate the site.
And speaking of navigation—back when I last overhauled my site, it was
to add navigation links (thanks to Eve, who convinced me to add them), about
half the XSLT I wrote was to support the navigation links
(as you can see from the examples above). I have an extensive array of navigation
links mostly hidden behind the <LINK> tags; if you
have Mozilla, you can
see them by enabling the “Site Navigation Bar” (View → Show/Hide → Site Navigation Bar). Quite a bit of
work for something of perhaps dubious value? We'll see …
Swapping disks
Tonight Mark and I
replaced a bad disk on swift, the colocated server currently
serving up our sites. The bad disk is the system disk; the websites
themselves (along with some other services we have) all reside on another
disk.
There was much discussion before heading over there as to the best way to
approach the problem of copying the data off the bad drive. The first
method would to be install the new disk into the machine and do a
disk-to-disk copy. The downside is that swift is a 1U system with no room for a
third drive (no matter how temporary). Also, the unit is designed to run
with the cover on—we were unsure how it would deal running uncovered. The
other option would be a network based copy, from swift to another
machine with the new drive in it. The problem here was speed—even though
we could hook the second machine directly to swift (on the
secondary ethernet port) at 100Mbps it would still take a while to copy over several gigs
worth of files. We decided to take a second computer (the Windows box Spring and I share) as
we decided to decide when we got to the colocation facility.
When we got there and examined swift, it was decided to use the
temporary computer and do a network copy. We had some difficulty in getting
the Windows box to recognize the new SCSI disk (Mark had some extra SCSI controllers and disks); it was
certainly news to me that the BIOS setup was on the harddrive instead of on the ROM (much like the very old days of
PCs). Once we straightened
that out, it was pretty straightforward to boot Gentoo from a live CD, partition and format the new drive.
Then it was time to copy the files. It took some work to figure out how
to use rsync using the rsync protocol and it still took us two
attempts to get everything (first time rsync ran without root
priviledges which limited the number of files copied). Once that finished
(and still on the temporary machine) we recompiled the kernel to support
SCSI, then set
about to make the drive bootable.
The problem here was that Gentoo was a bit too aggressive in
identifying hardware, and since the Linux kernel sticks USB storage devices under the
SCSI layer, the
harddrive ended up with an ID that it wouldn't have in the swift.
We ended up having to reboot the Gentoo CD, remove the loaded USB drivers, then mount the SCSI drive, then make the drive bootable. Once
that was done, the temporary system booted up without a problem.
We then removed the drive and controller, cleaned the area (so we could have room to move about) and spent a few minutes making a game plan of swapping the bad drive for the new one. The physical swap went fairly smoothly. It was reconfiguring the BIOS that proved to be rather difficult. We couldn't get into the BIOS configuration. A search of possible key sequences to get into the BIOS configuration revealed:
- DEL
- F1
- F2
- F10
- Ctrl-Alt-Esc
- Ctrl-Esc
- Alt-Esc
- INS
- Esc
- Ctrl-Alt-Ins
We ran down the entire list, and not one worked. Mark then had the brainstorm to hold down the keys as the machine was powered up. First key he tried, DEL got us into the BIOS.
Talk about having plenty of time to get into the BIOS configuration.
Once the BIOS was configured with the new drive, it rebooted without a problem.
All told, we spent maybe five hours doing the drive swap, with the websites unavailable for maybe fifteen minutes tops. It was a bit scary at times though, watching the copying go with numerous disk errors. But so far, nothing important seems to have been corrupted, unlike most of the files in Mark's home directory (but he had current backups of that data anyway).
Tuesday, January 27, 2004
Hello world! Care to read your email?
Yes, this really is the classic program that prints “Hello, world!” when you run it. Unlike the elementary version often presented in books like K&R, GNU hello processes its argument list to modify its behavior, supports internationalization , and includes a mail reader.
hello - GNU Project - Free Software Foundation
Every program attempts to expand until it can read mail. Those programs which cannot so expand are replaced by ones which can.
Law of Software Envelopment
I didn't even realize GNU had a “Hello world” program available for downloading, much less one that succumbed to the Law of Software Envelopment. Granted, GNU then goes on to say:
The primary purpose of this program is to demonstrate how to write other programs that do these things; it serves as a model for all of the GNU coding standards.
It's quite amusing that GNU can turn this:
#include <stdio.h>
main()
{
printf("hello, world\n");
}
into a 400k compressed download, complete with its own configuration
script, m4 macros (who uses m4 anymore?),
man pages (and here I thought GNU was big on info pages) along with documentation
in TeX, plus the various
language files for Russian, Slovanian, Japanese and I even think English is
included in there somewhere.
Quite amusing.
Note: technically, the code should be written as:
#include <stdio.h>
#include <stdlib.h>
int main(void)
{
printf("hello, world\n");
return(EXIT_SUCCESS);
}
to be fully ANSI compliant, but hey, who am I to argue with the authors of C?
Then again, if you really want to be anal retentive about it, then:
#include <stdio.h>
#include <stdlib.h>
int main(void)
{
(void)printf("hello, world\n");
return(EXIT_SUCCESS);
}
But that's just being silly …
Oops
Yet another SYN flood to contend with, and yet again, it's
the same extortionists that took this company last year for quite a
bit of money (and I have to wonder—how do they note this in their
financials? “Unexpected hiring of Russian Security Consultants”?) that
“promised” protection for (I think) a year or so against such attacks.
One it was brought to their attention, the attack subsided.
But in the mean time, I was tasked to move several of the larger sites
still on the Boca Raton servers to the ones down in Miami. The intent of
the Miami servers is for each to act as a backup of the other (and the Boca
Raton servers will eventually act as a backup for the Miami servers) so in
the process of creating the accounts needed on the two servers I made a
slight mistake. Nothing bad, like an errant rm -rf * or
attempting to restart the network remotely. Nope. Just a simple
overwriting of /etc/passwd with the wrong file.
Nothing major. It just meant that no one could log into the
system. I didn't notice until I attempted to copy over some more files and
they failed. Or rather, I think scp or rsync
started asking for passwords when I explicitely set up a trust mechanism
between the two servers on their private network interfaces. I started
poking around on the server with the munged /etc/passwd file
and it came quite apparent what happened.
Fortunately, I still logged into the server with the munged
/etc/passwd file.
Unfortunately, I was not root. Nor could I become
root. This was not good.
Can't ssh since the authentication was blown. Which meant
that scp wouldn't work either. I thought maybe
rsync would work, but then I realized I set up
rsync to use ssh and since authentication didn't
work … (not that I realized until after trying rsync).
That's when I realized that a trip down to Miami might be required.
Several hours worth of driving for less than a minutes worth of work to
restore /etc/passwd. It was then I had a brainstorm …
why not hack my way back to root? Wasn't illegal—I was, after
all, the administrator for the system, and I had local
access, which would make it easier than a remote exploit.
One Google search later, and I'm perusing 0day-exploits. Downloaded a few, got the code to the borked server, compile, run and nothing. Download another one, get it on the server, compile, run, and nothing.
Damn you, Gentoo, I thought, and your custom compiliation installs! I can't even hack my way back into the system!
I supposed I could have kept at it, but at there comes a time of diminishing returns, which would be the time it would take me to drive to Miami, reboot the server into single user mode, restore the file, reboot and drive back home. The drive and reboot is the simpler solution in this case (if a bit tedious); had the server been on the other side of the country, then yes, maybe I would have stuck with the hacking attempt a bit longer …
Wednesday, January 28, 2004
What type of data center doesn't have a crash cart?
Dispite my trying to avoid it, I had to drive down to Miami to reboot a server into single user mode, copy a file, then reboot it back into normal operations. To make it even more surreal, I was informed that the Miami NAP does not have a crash cart on the premises.
What type of data center does not have a crash cart?
And in case you are wondering what a “crash cart” is, it's a cart that has a monitor, keyboard and mouse that you can push around to hook up to a computer in case you need to locally check a server. A top of the line crash cart can't cost more than a grand, and given that the Miami NAP is nothing more than a six story data center you would expect (okay, I would expect) them to have at least one crash cart.
So not only did I have to drive an hour south to Miami to reboot a server, but I had to carry along a monitor and keyboard with me.
Sheesh.
I ended up lashing a monitor and keyboard with rope to The Kids' luggage cart (since the bungee cords have long since been lost). Servicable, but still took about twenty minutes to do the lashing. The drive down to Miami wasn't bad, but as I eyed northbound I-95 I knew I would be in for a long drive home.
Once I arrived at the Maimi NAP, it took over half an hour to locate the appropriate cabinet. I knew the cabinet was on the second floor, but past that, it was a maze of twisty passages, all alike. There were two of us, myself and a security guard, walking up and down rows of racks. Eventually the security guard found the right cabinet.
Several minutes to set up the monitor and keyboard. Reboot twice, since
I found out the hard way that the timeout value to boot into single user
mode was about two seconds, if that. Then it was a matter of copying a
backup of /etc/passwd into place, reboot, test, and two minutes
later, done. Then fifteen minutes or so lashing the monitor and keyboard
back to the cart, finding my way out of the labrynth and a long slow drive
home.
And I ask again: what type of data center doesn't have a crash cart?
Thursday, January 29, 2004
Aspirin for computers
Difference of expectations.
Not once in nearly 20 years of computing have any of my computers received a virus. Oh sure, I captured and disassembled a few computer virii during an outbreak at FAU in 1988 (and I still have the disks—amusing to think they might still work after all this time) but an actual outbreak on any system I've owned?
Nope.
So it was rather surprising to find Spring installing Norton Anti-Virus on the system we both share.
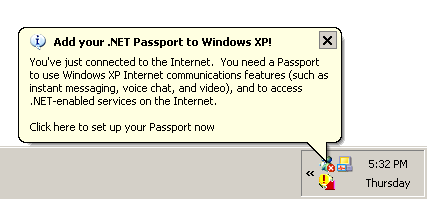 But Spring has had the
rather unfortunate experience of having her computer infected with a virus.
And she was installing Norton because she was scared of what would happen if
I found the computer infected. I have to remind myself it's the
thought that counts, because afterwards, I found the computer nearly
unusable (and I was definitely being too snarky over this).
But Spring has had the
rather unfortunate experience of having her computer infected with a virus.
And she was installing Norton because she was scared of what would happen if
I found the computer infected. I have to remind myself it's the
thought that counts, because afterwards, I found the computer nearly
unusable (and I was definitely being too snarky over this).
I have a hard time wrapping my brain around the fact that a 2.2 GHz machine can feel slow. But that's what happened after Norton was installed.
And it started pimping for Microsoft Passport for some odd reason, and tossed in the Microsoft Messenger in the system tray, which is damn impossible to turn off because, and I quote:
There are other applications currently using features provided by Windows Messenger. You must close these other applications before you can exit Windows Messenger. These applications may include Outlook, Outlook Express, MSN Explorer, and Internet Explorer.
Lord knows what's using it, because Outlook, Outlook Express, MSN Explorer or Internet Explorer sure aren't running, as far as I can tell. I got it to shut up about getting Passport, but that's about it.
And did I mention the system feels sluggish?
It's the thought that counts.
That, and I can disable Norton, which seems to help.
Friday, January 30, 2004
Non testing of old features
Switching SMTP servers will always cause problems. When we first switched to Postfix, I had problems with the email interface for mod_blog. It turned out that postfix set the default permissions of child processes to be restrictive and the patch was to relax the default permissions.
Of course, I forgot about that with the software I wrote for Spring.
But it didn't really matter since she rarely, if ever, used the email interface.
Until today.
It took me quite a while to track down the problem and add a one line fix.
A Toy Party
 Spring is now a
distributor for Discovery Toys, and
tonight was her first party, where toys are displayed and sold. The toys
themselves are educational in nature, and I found myself having quite a bit
of fun with the Markbleworks Raceway Construction Set.
Spring is now a
distributor for Discovery Toys, and
tonight was her first party, where toys are displayed and sold. The toys
themselves are educational in nature, and I found myself having quite a bit
of fun with the Markbleworks Raceway Construction Set.
The party itself was small, Spring's sponsor, Kelly, Gus and Angel but quite successful given the small turnout.
Saturday, January 31, 2004
The difference between a bad hair cut and a good hair cut
What's the difference between a bad haircut and a good one?
Two weeks.
Thank you. I'll be here all week. Try the veal!
I finally got fed up enough to take the professional clippers we have, snap on the inch guide, and weigh the consequences between having this horrible feathered hair from the 70s or removing several pounds of hair from the top of my head and get it out of my eyes.
I stood there for several seconds, knowing that once I started there was no going back.
What the heck! It's only two weeks!
And no, no pictures until I have a good haircut.
Drawing economics
Mark Lombardi (1951–2000) was an artist whose studio practice involved the obsessive tracking of just such mass corporate and political malfeasance. Pursuing his stories through various public-domain sources, Lombardi created exquisitely geometrical, airily complex pencil drawings that trace the connections and chronologies underlying corporate fiascoes like the failure of the Bank of Credit and Commerce International (BCCI), the looting of the Savings and Loan industry, the internecine duplicity of the Banca Nazionale del Lavoro and the Vatican, or the affairs of Bill Clintons Arkansas cronies the Lippo Group. Blending pop assumptions with conceptualist technique, and approaching the art/life divide as if it were a panel of mirrored glass, Lombardi made a practice of updating his drawings when new facts in a given story came to light. Were he alive now, he would surely be composing a new version of a small work begun in 1999 called George W. Bush, Harken Energy and Jackson Stephens, c. 1979-90, 5th Version (1999).
Via racoon: notes and scavagings, Relatable: Mark Lombardi Draws Economics
Very cool art. Who thought one could draw economics?
Is the Superbowl over yet?
I will be so glad when Superbowl Sunday is over.
Yet more attacks against the servers.
Sigh.
![Enough hair to make a cat [Enough hair to make a cat]](/2004/01/31/thumb.hairball1.jpg)
![Or supply the Hairclub for Men [Or supply the Hairclub for Men]](/2004/01/31/thumb.hairball2.jpg)

![Glasses. Titanium, not steel. [Self-portrait with my new glasses]](https://www.conman.org/people/spc/about/2025/0925.t.jpg)